
Enhancing Digital Signatures: The Transition to PSS
Enhancing Digital Signatures: The Transition to PSS 관련
Now that you understand how OAEP transformed RSA encryption by mitigating vulnerabilities in deterministic padding, it’s time to turn our attention to RSA digital signatures - a critical function for ensuring message integrity and authenticity.
Early RSA signature schemes suffered from similar problems as raw encryption: their deterministic nature made them prone to forgery and replay attacks. This vulnerability paved the way for an improvement: the Probabilistic Signature Scheme (PSS).
Before we dive into PSS itself, let’s quickly understand the pain points with early RSA signatures.
Problems with Early RSA Signature Schemes
Traditional RSA signatures were generated by simply applying the RSA decryption function on a message digest (often with minimal formatting):
where m is the hash (or encoded hash) of the message. This approach was deterministic which meant that each time the same message was signed, the exact signature was produced. Such determinism had two major drawbacks:
1. Predictability and Replay
Since the signature for a given message was always identical, an attacker could replay a captured signature with impunity or forge signatures if they could deduce patterns in the signature scheme.
2. Forgery Risks
In a deterministic setting, if an attacker finds any structure or mathematical relationship in the signature, they might be able to forge a valid signature for a new message. In certain scenarios, weak formatting could allow an adversary to create a “signature transformation” that produces a valid signature without having access to the private key.
These issues highlighted that a signature scheme must be probabilistic to be secure against adaptive forgery attempts and to ensure non-repudiation. This means that the signer should not be able to repudiate a signature because it is bound to a random value known only at signing time.
Birth of the Probabilistic Signature Scheme (PSS)
Towards the end of 1998, Bellare and Rogaway also proposed a scheme to overcome the inherent limitations of deterministic RSA signatures[1]. The core idea was to introduce randomness into the signature generation process so that even when signing the same message twice, the resulting signatures would be different. This randomness comes from a salt value and a carefully designed encoding process. The result is a signature method with strong, provable security guarantees.
This randomness prevents attackers from exploiting patterns in the signature process. The probabilistic Signature Scheme was designed to be provably secure in the random oracle model, meaning that forging a signature would be as hard as breaking RSA itself under certain assumptions[2].
The block diagram below is a visual representation of the PSS encoding schema:
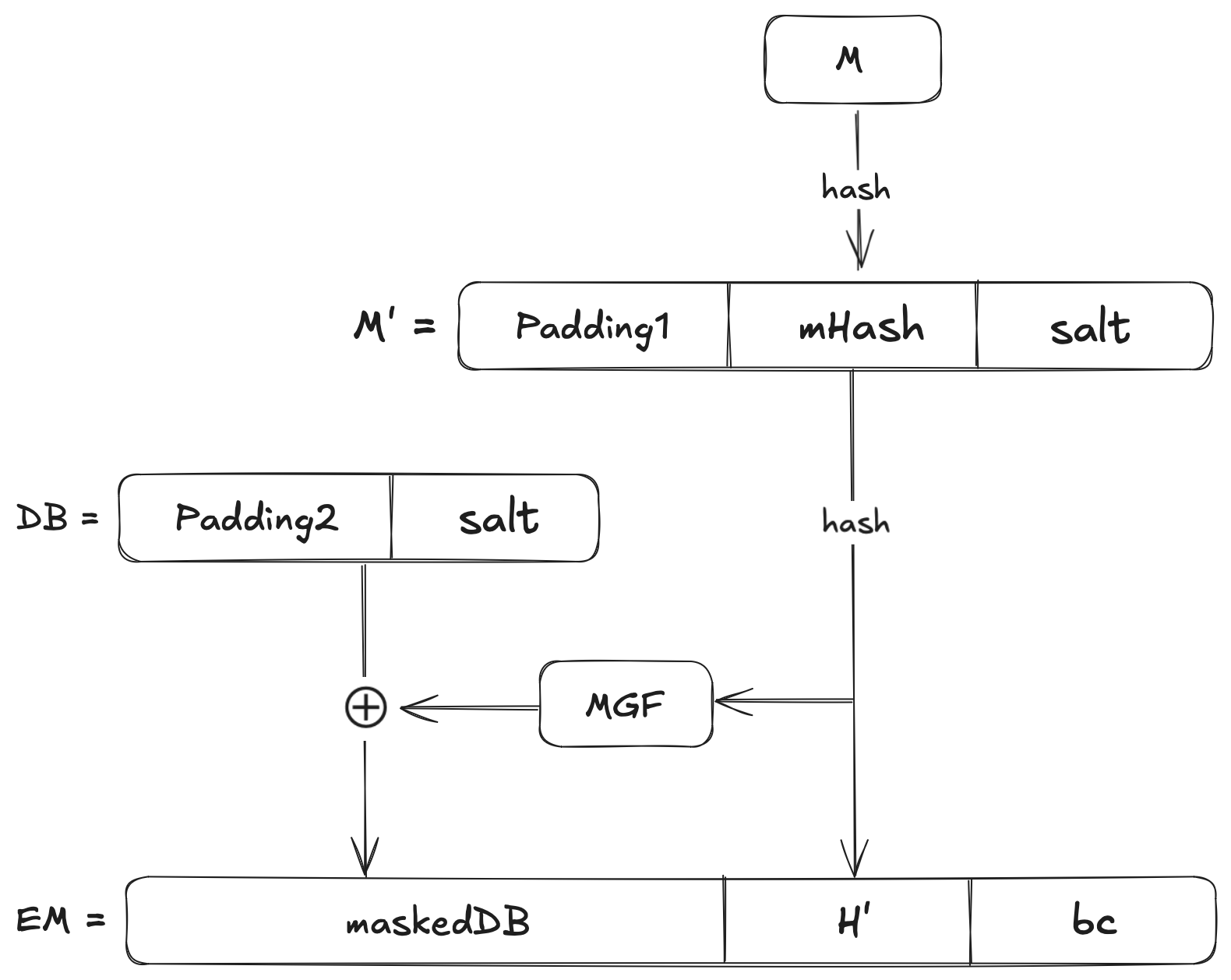
Let’s understand what these mathematical notions mean as well as the workings of RSA-PSS, up next.
The Mathematics Behind PSS
Before diving into the mechanics of RSA-PSS, it’s helpful to define the notations and terms you’ll see in the steps ahead.
In RSA, is the modulus, a large integer that is the product of two primes. is the length of in bytes. For an 2048-bit key, bytes.
represents the message data or document you want to sign. In RSA-PSS, you’ll typically first compute a hash of . Hash refers to a cryptographic hash function (for example, SHA-256) that maps data to a fixed-size output. The output length is denoted . For SHA-256, .
We will use a salt, , randomly generated string of fixed length (often the same as ). This randomness is essential in ensuring that each signature is unique, even for the same message.
or is the hash of the message and is a secondary hash that includes both and the salt . This appears in the PSS encoding step.
The Mask Generation Function, , is a function that uses the hash internally to produce a pseudorandom output of arbitrary length. In PSS, it is used to “mask” parts of the data block so that the signature is hard to forge.
A fixed byte, (in hex) is appended at the end of the encoded message to mark the boundary of the PSS structure. This serves as a simple integrity check during decoding. After a successful encoding we receive an encoded message which is an octet string of length .
Now that you are familiar with all the necessary notations, we are ready to begin the encoding step.
Step 1: Message Hashing and Salt Generation
We compute the hash of the message as where is our message. We will also create a random salt (of fixed length, say 20 bytes if you use SHA-1).
Step 2: Encoding the Hash with the Salt (PSS-Encode)
We will construct a Data Block, , by combining a padding with the hash and the salt. The padding is a sequence of ’s that fills space and ensures a fixed length. Mathematically:
Now we compute the Hash of this block as . We will generate another octet string and concatenate it with the salt and as a delimiter:
Note that is an octet string of length . The mask that you see in the visual representation above must be of this length. Mathematically:
We will then apply this mask on the block using an operation to produce our maskedDB:
Recollect that is the intended length of the Encoded Message and hLen is the length of the hash output. Now we append a fixed trailer field and produce the encoded message in its octet string representation:
This encoding process ensures that both the salt and the hash are mixed together in a non-reversible, pseudorandom manner. The randomness from the salt is “spread” over the data block by the , making it extremely difficult for any adversary to manipulate the signature.
Step 3: RSA Signature Generation
Once you have the encoded message , the RSA signature is produced by using the RSA private key. First, convert the Octet String to its integer representation using the OS2IP method we’ve discussed before. Then apply the RSA Private Key Operation:
where is the private exponent and is the RSA modulus.
Step 4: Signature Verification
At the receiver end, when any recipient wants to verify a signature, they reverse the process:
- Probabilistic signature scheme ↩︎
RFC 8017: RSASSA-PSS ↩︎