
Exploiting Textbook RSA’s Determinism and Malleability
Exploiting Textbook RSA’s Determinism and Malleability 관련
Key Generation (Setup)
For our toy example, we’ll choose small prime numbers and generate an RSA key pair:
Let’s select the values of and . Both of these values are prime. Now, compute the modulus and Totient Function as follows:
Now choose the public exponent. Let’s consider since it is coprime with , and . Now let’s compute the private exponent. We know that is the modular inverse of . We need to find such that . Using this knowledge we can compute as .
Finally, the public key is (, ) and the private key (secret) is .
Encryption Process
Now, let’s encrypt a simple message using the above key. Let us select our plaintext to be . The cipher text in this case would be:
To consolidate the findings so far, if we encrypt message with the public key , we will produce the cipher text . Now, let’s try the exploits.
Determinism Exploit (Ciphertext Guessing Attack)
Textbook RSA is deterministic - the same plaintext always yields the same ciphertext (with no randomness involved). An attacker who intercepts the ciphertext can exploit this by encrypting likely plaintext guesses and comparing results:
The adversary, say Eve, will try encrypting candidate plaintexts with the public key and see which one produces . They may pick randomized values to increase their efficiency:
By simply comparing ciphertexts, the attacker finds that encrypting yields , which matches the intercepted ciphertext. Thus, the attacker learns the original plaintext was . This is possible because there’s no randomization in textbook RSA - an eavesdropper can identify a message by trial encryption of guesses, breaking confidentiality if the message space is small or guessable.
Malleability Exploit (Ciphertext Manipulation Attack)
Raw RSA is also malleable. This means an attacker can take a ciphertext and modify it in a way that results in a predictable change in the decrypted plaintext. Let’s understand how this works.
RSA has a multiplicative property, that is, multiplying two ciphertexts corresponds to multiplying their plaintexts before encryption:
The sequence diagram below explains how the malleability exploit works in naive RSA.
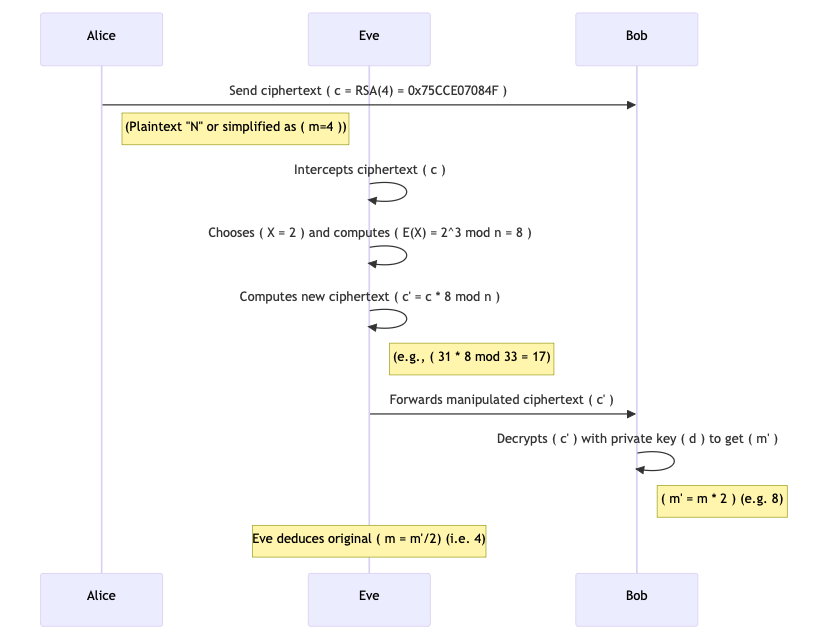
Alice sends a ciphertext to Bob after the initialization phase. Note that by this point, and are public knowledge. Eve intercepts this ciphertext by using mechanisms such as a MiTM (Man in the Middle) attack.
Now, Eve picks a known value to manipulate the message. Let’s say the attacker chooses (with the intent to double the original plaintext).
Then they compute the encryption of using the public key:
Now, Eve multiplies the original ciphertext by this value () to get a new ciphertext:
This new ciphertext is the encryption of the product of the original plaintext and . If we directly encrypted with RSA, we would get . This means that corresponds to the plaintext , which is the original message multiplied by .
In a real-world chosen ciphertext attack, the attacker may have access to a decryption oracle or observe a system response that reveals information about . The decryption result 8 is exactly (the original message multiplied by the attacker’s chosen factor). Knowing the factor , the attacker can deduce the original message by dividing: . Note that Eve has not broken the mathematical foundations behind RSA here. They have only used the public key to compute an encryption of , and then combined it with the intercepted ciphertext. They don’t know the original plaintext yet, but they have manipulated the ciphertext in a way that they know the new plaintext is twice the original message.