RSA Operations
RSA Operations 관련
Now that the mathematical foundations are laid, the RSA algorithm can be seen as a set of three core operations: Encryption, Decryption, and Signing. Throughout this handbook's next sections, we will critically analyze these operations and learn about several pitfalls in each. Then we will examine how these were averted with the birth of new schemes, each to solve a new issue discovered on the way.
Encryption
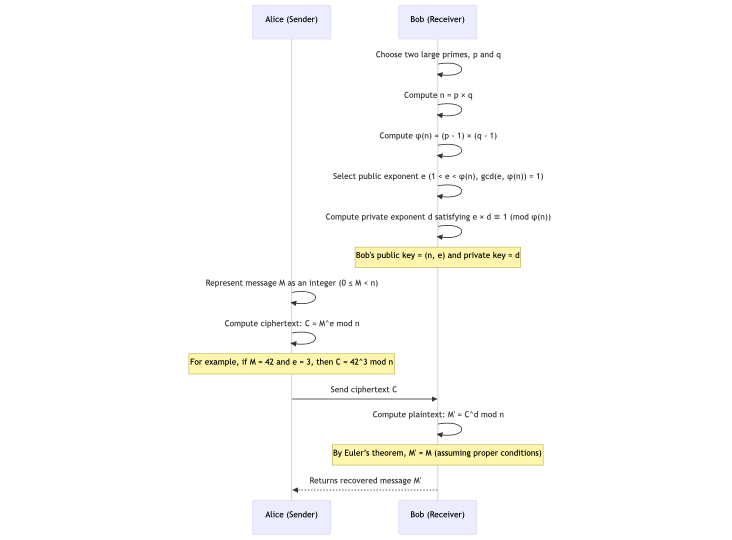
With the public key available to everyone, any user can encrypt a message (where is first encoded as an integer in the range ) using the formula:
Here, is the ciphertext. Because the operation is based on modular exponentiation, even if is known, recovering from without knowing is computationally hard.
Decryption
The intended recipient, who possesses the private key , decrypts the cipher text by computing:
Using the relationship and properties from Euler’s theorem, the above operation exactly inverts the encryption step, recovering the original message .
This ensures that only the holder of the private key can read the encrypted message. This is the backbone of RSA’s use in secure communication.
The sequence diagram below wraps up our discussion so far:
Digital Signatures
Digital signatures fulfill a different security goal: authenticity and integrity rather than confidentiality. While encryption and decryption use the public key for “locking” and the private key for “unlocking,” digital signatures reverse these roles.
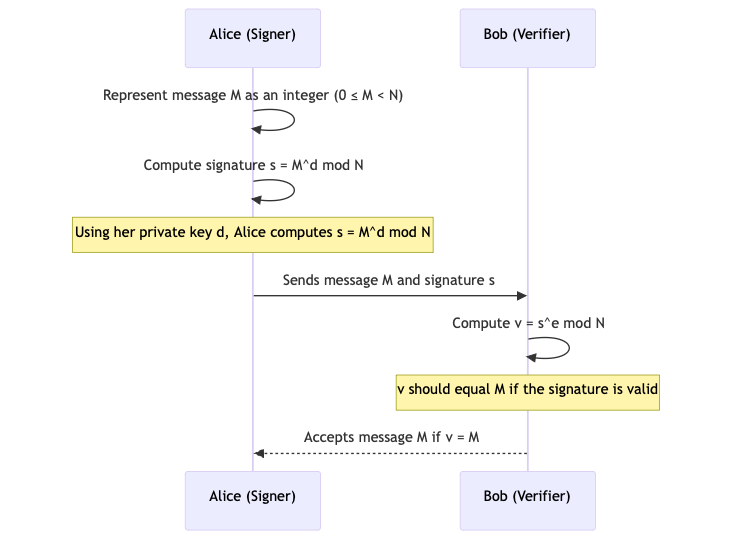
1. Signing
The author of a message uses their private key to compute a signature on the message , guided by the formula mentioned below:
This can later be verified by others using the corresponding public key. The purpose here is not to recover a secret message but to create a proof of authenticity.
2. Verification
Anyone with the public key can verify that the signature indeed belongs to the message by computing:
If the equivalence holds, it confirms two key points: That the message has not been tampered with (that is, integrity), and that the signature must have been generated using the private key (that is, authenticity).
As long as is kept secret, only the legitimate signer can produce a valid signature. Take at look at the sequence diagram below to understand the complete process.