
The Bleichenbacher Attack
The Bleichenbacher Attack 관련
In 1998, Daniel Bleichenbacher published a seminal paper[^8] demonstrating an adaptive chosen-ciphertext attack against RSA with PKCS#1 v1.5 padding. The Bleichenbacher Attack, also dubbed as the “million messages” attack, demonstrated that if an attacker has access to an oracle that tells whether a submitted ciphertext decrypts to a properly padded plaintext (that is, whether the PKCS#1 v1.5 formatting is correct), the attacker can gradually recover the full plaintext. Let’s break down how this attack works:
First, Eve needs an Oracle. The attack assumes the attacker can query a system, such as an SSL/TLS server, and find out if a given ciphertext is PKCS#1 v1.5 conformant. In the 1998 paper, Bleichenbacher exploited the fact that a TLS server, when presented with an improperly padded RSA-encrypted premaster secret, would respond with a specific error alert if the padding was wrong. Essentially, the server acted as an oracle: it would decrypt with its private key and simply tell the attacker “padding OK” or “padding error” (the error could be timing-based or an explicit alert).
Note that the oracle does not reveal the plaintext. It only reveals a single bit of information at a time: “valid padding or not.” This might seem harmless, but Bleichenbacher showed that it’s enough to eventually recover the plaintext.
To quickly recap, the attacker’s goal is to find the unknown message integer (the PKCS#1-padded plaintext as an integer) given its ciphertext , using the oracle. We know that if is properly padded, it lies in a specific numeric range: where , as defined earlier.
If , then , and a correctly padded will start with , so it’s between and . The attacker, Eve, initially only knows that is in the range .
In the Bleichenbacher Attack, Eve will exploit RSA’s multiplicative property. They will choose a number (called the multiplier) and compute a new ciphertext . This here corresponds to a new plaintext: (because ).
To begin the attack, Eve finds some such that yields a valid padding. This is referred to as the Blinding step. This is usually easy - for example, can be chosen so that is just slightly above , which almost certainly will wrap around and land in . The attacker does not know m to verify this directly. They rely on the padding oracle’s yes/no response to infer that the blinded plaintext falls in the correct range.
If the oracle returns “valid padding” for a given , it tells the attacker that lies between and . Mathematically:
Now, Eve will try to try to narrow down this range in a loop, which is often referred to as the interval having step. Initially, Eve had one wide interval that contains . In each iteration, Eve tries increasing values of (starting from a certain minimum) until the oracle returns “padding OK” for . Suppose this happens at some . Given this feedback, Eve now knows:
This congruence implies there exists some integer such that:
Rearranging, we get a constraint on :
Eve doesn’t know outright, but they can solve for the possible range of by considering the current interval for m. Essentially, Eve uses the previous bounds on to guess which would make the inequality true, then updates the new bounds as the intersection of all possible solutions for . This dramatically shrinks the interval.
Each oracle query yields such a constraint. Eventually, the interval collapses to a single value, . Now, Eve can find the plaintext using:
At that point, Eve has recovered the entire padded plaintext , and by stripping off the padding, the original message itself.
The sequence diagram below consolidates our learning of the attack:
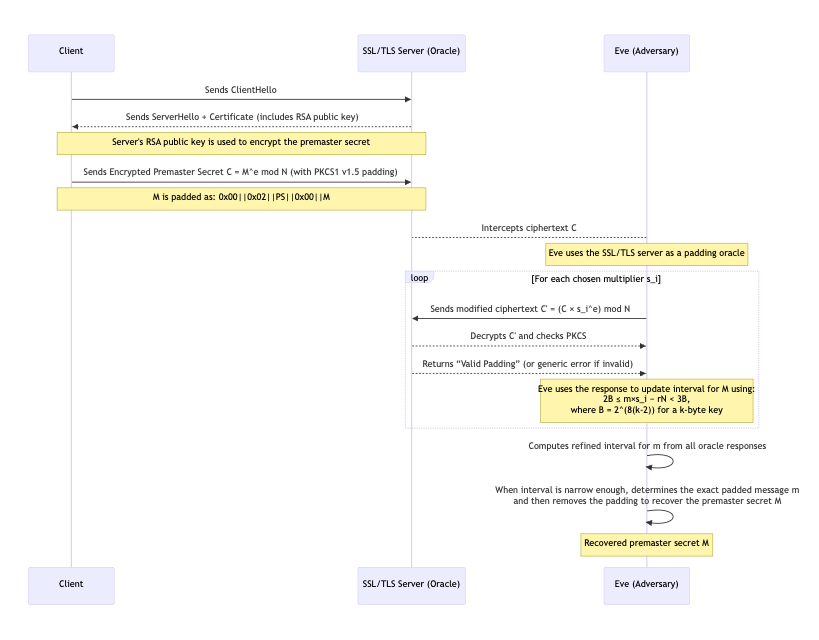
The Bleichenbacher attack showed that the format of the padding in PKCS#1 v1.5 leaked just enough info to enable a full private-key operation (decrypting the message) without ever factoring . The attack leveraged the fact that it’s possible to craft ciphertexts that will decrypt to a valid-looking plaintext without knowing the plaintext. In essence, PKCS#1 v1.5 padding allowed about in chance (roughly) for a random blob to appear as “valid padding.” That was enough for an adaptive attack to succeed with feasible queries.
This is precisely what later padding designs like OAEP fixed. OAEP’s design makes such random valid ciphertexts astronomically unlikely (plaintext aware). We will learn about RSA-OAEP in the next sections.
To mitigate the Bleichenbacher attack without immediately changing the padding scheme, practitioners implemented defensive measures. For example, TLS should treat all decryption failures the same way (so an attacker can’t distinguish padding vs. other errors), and servers would generate a fake premaster secret on padding failure to continue the handshake and avoid timing leaks. Nonetheless, the safest course has been to deprecate PKCS#1 v1.5 encryption in favor of schemes like RSA-OAEP.