
How to Build Your Own Private Hacking Lab with VirtualBox
How to Build Your Own Private Hacking Lab with VirtualBox 관련



Ethical hacking involves testing and finding vulnerabilities in systems. But doing this on live networks or public servers can lead to accidental damage.
Setting up a virtual lab for hacking is a great way to sharpen your skills in a safe environment. A private lab ensures that all your activities remain isolated, so there’s no risk of harming real systems or violating legal boundaries. It allows you to make mistakes and learn from them without causing harm.
Project Setup
This guide will teach you how to set up your own private lab. To do this, we’ll need three things:
- Virtualization software
- Attacking Machine
- Target Machine
Virtualization software allows one physical computer to run multiple virtual machines (VMs). A virtual machine acts like a separate computer with its own operating system and programs but runs on the same hardware as the host computer.
VirtualBox is a popular virtualization software. VMware is another alternative.
To practice hacking, you need two machines — an attacking machine and a target machine.
You can use your own system as the attacking machine. But it is better to use a machine like Kali or Parrot which comes pre-installed with all the tools you will need.
For the target machine, we can use a repository like Vulnhub. It contains several VMs built for you to practise your skills. Each one is designed to have a vulnerability that you can practise exploiting.
The downloads required for this setup are quite large, so I recommend you download and keep them ready.
- Download VirtualBox (download the extension pack as well)
- Download Kali (64-bit Virtualbox image)
- Download Mr Robot vulnerable machine
Let’s go 👉
How to Install VirtualBox
To download VirtualBox, go to the downloads page. Based on your operating system, download the package and install it.
Once installation is complete, you should see a similar page depending on your operating system.
Double-click on the extension pack and make sure its installed as well.
How to Install Kali Linux
Now let’s install our attacking machine. Extract the .7z file from the Kali Linux download. Then click the green “Add” icon on the VirtualBox interface and point to the .vbox file.
.vbox fileAll the default settings will be applied and you should have the attacking machine installed. If you are stuck, you can find detailed instructions here.
Don’t start the machine yet. Let’s add the target machine as well, followed by changing a few networking settings. Then we can start hacking.
How to Install a Target VM
Now let’s install the target. Double-click on the downloaded mrRobot.ova file. Use the default settings and click “Finish”.
Once both the attacking and target machines are setup, you should see them both in the machines list.
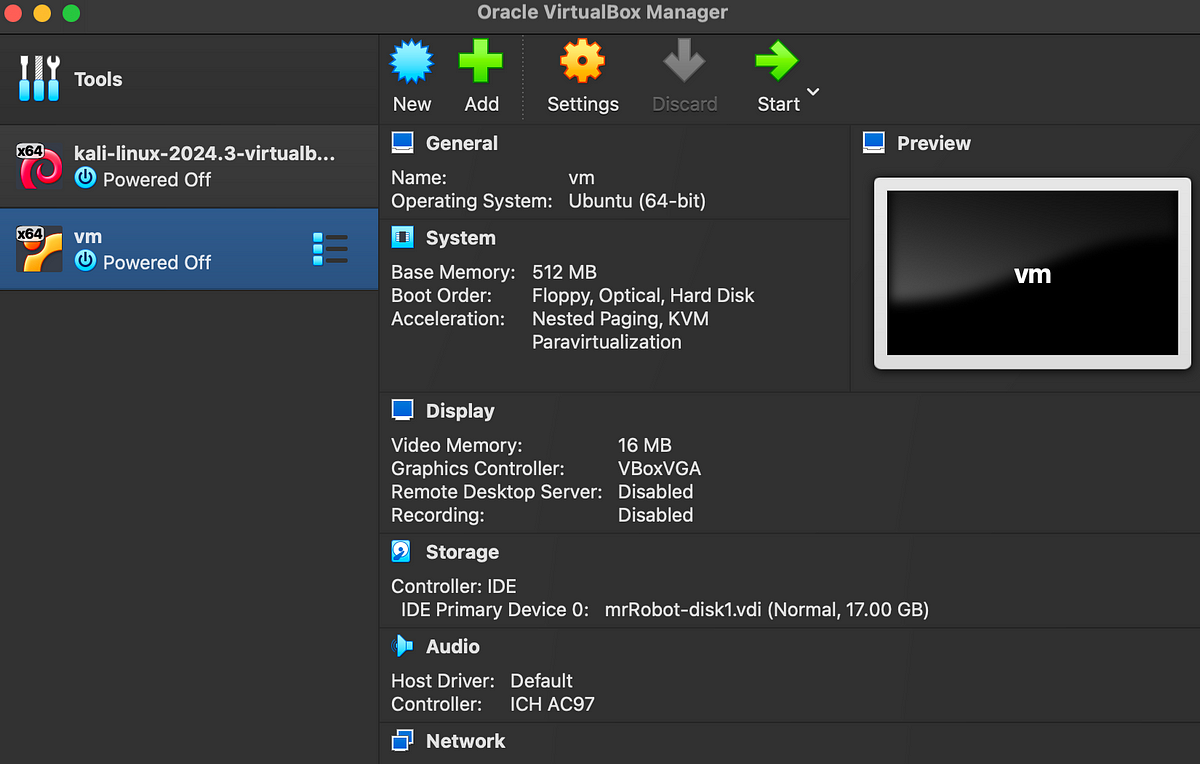
Now let’s update the network settings to make sure our VMs are secure.
Update Networking Settings
There are many ways to set up a network in VirtualBox. But in our case, we want to isolate our lab from the public internet. The best way to do this is to set up a host-only network.
In a host-only network, the VMs can communicate with each other but not the public internet. Let’s set it up.
In the Virtualbox interface, click on “Tools” and click “Host-only Networks”. Then click “Create”. It will automatically create a host only network with an IP range. For simplicity, let’s change the network’s name to “MyHackingLabNetwork”.
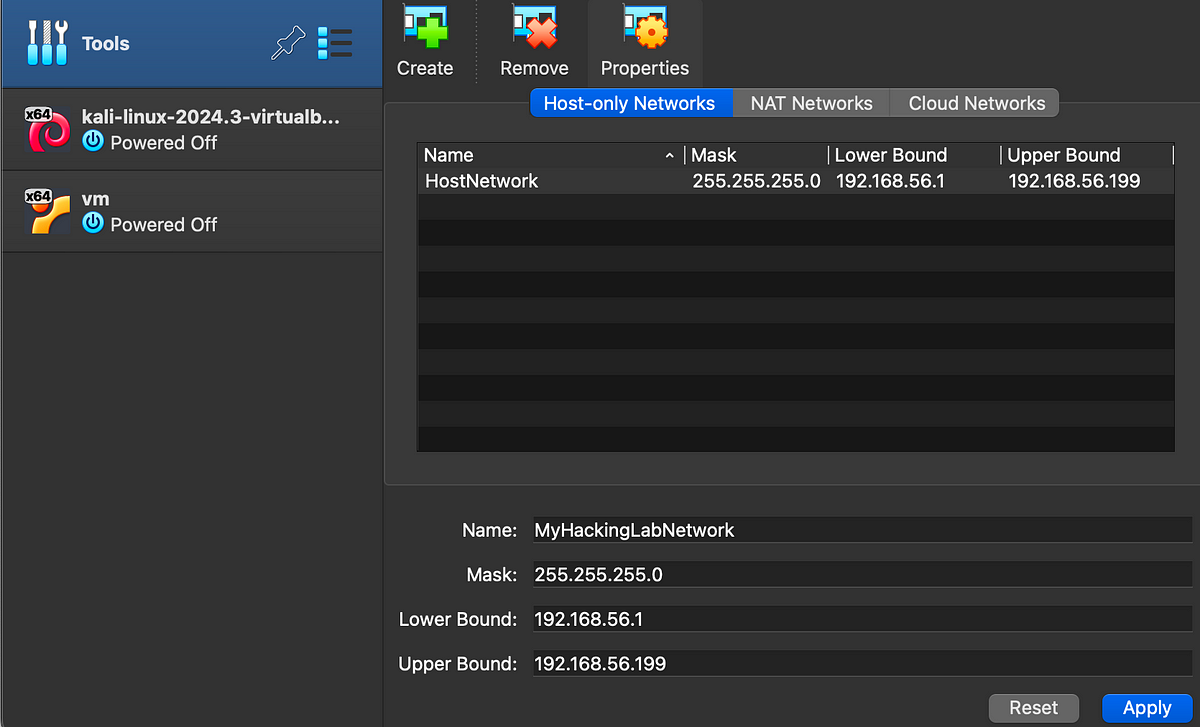
Click “Apply”. Now we have a host only network. Next, let’s configure our virtual machines to connect to this network.
Click on the Virtual Machine and click “Settings” icon. Under “Network”, choose “host-only network” and choose the name as “MyHackingLabNetwork”. Click “OK” once done.
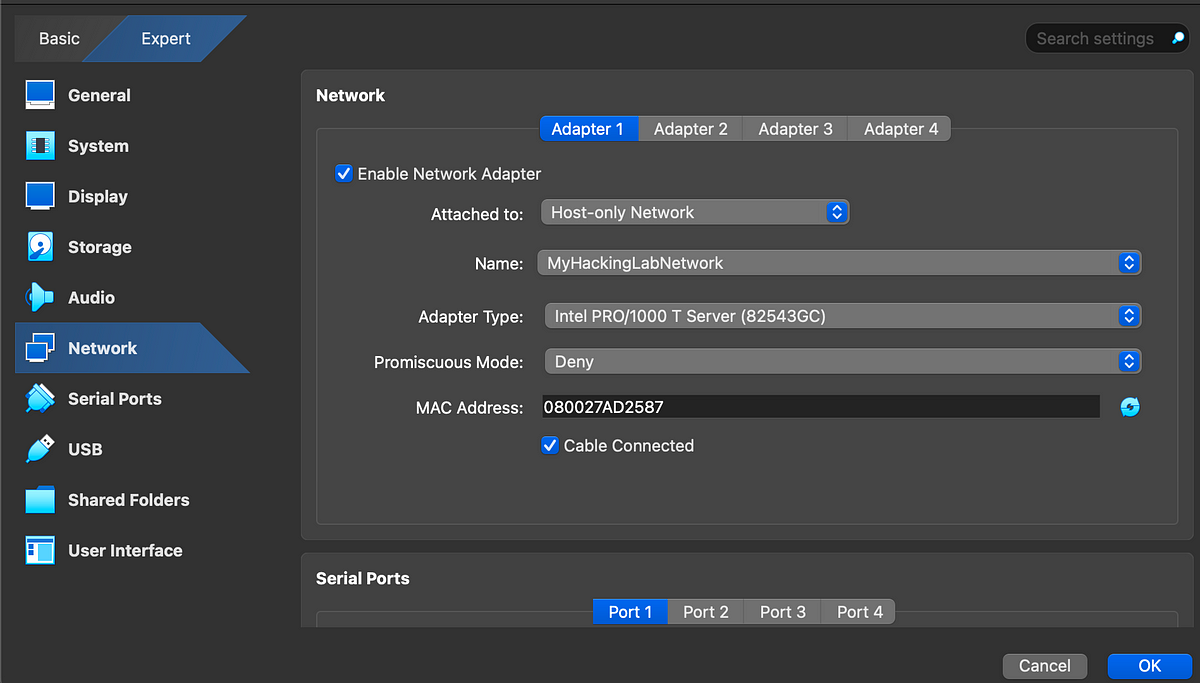
Do the same for the target machine. The IP addresses for these virtual machines will automatically be assigned by our “host-only” network.
Scanning the Target
Now we are ready to go. Power on both machines.
Note
Both machines will show a default option to startup - just press Enter. If the VM looks small on your screen, click View -> Scaled Mode on the top menu.
The username and password for the Kali machine is “kali”.
You should see the Kali Linux UI as below.
For the Mr.Robot box, you should see the following UI:
Now let’s find the IP addresses of these machines.
In Kali, open a terminal and type ifconfig | grep inet.
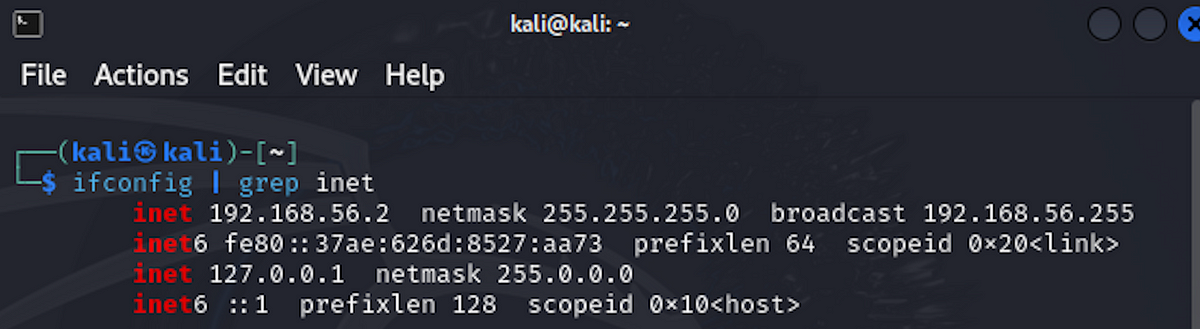
You should see an IP address similar to 192.168.56.x. This is the IP of the target machine.
Now let’s use nmap to scan for other machines in this network. If you don't know what Nmap is, here is a tutorial.
Let’s do a ping scan from Kali to look for other machines in the network. Run the following command:
nmap -sn 192.168.56.0/24
This command pings all IP addresses from 192.168.56.1 to 192.168.56.254 to see what is up and running. You should see three similar results.
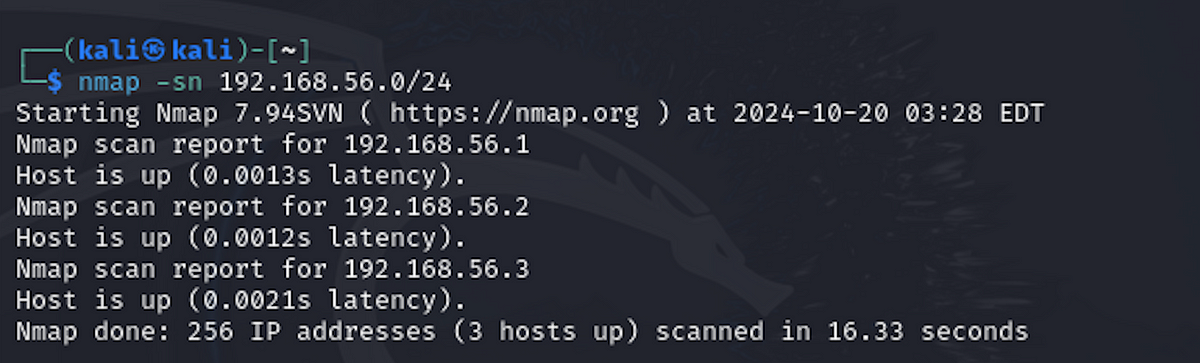
The first result is usually the IP of the adapter. So we can ignore it. Out of the two, one of them is the IP of our attack machine. We are interested in the third. In this case, its 192.168.56.3. Let’s do a service version scan of this IP and see what comes up.
nmap -sV 192.168.56.3
You should see a similar result as below if you are scanning the Mr.Robot virtual machine:
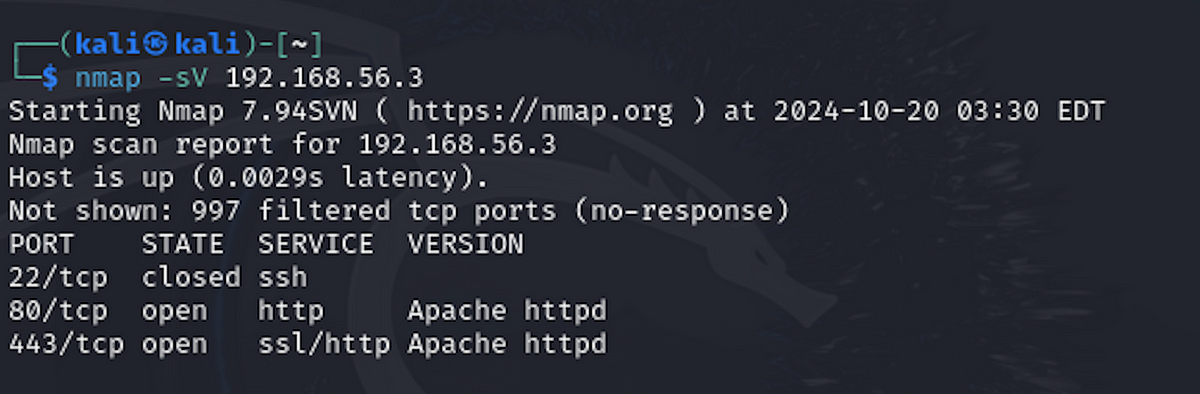
The above image shows that there are three ports on the server. One of them is ssh, which is closed. The other two are web server ports - 80 for http and 443 for https.
Conclusion
Congratulations! You’ve successfully set up your own hacking lab using VMware. This lab gives you the flexibility to practice ethical hacking in a controlled, isolated environment.
For more free tutorials on cybersecurity, join our newsletter. To learn how to hack the Mr.Robot and other boxes, join our private community Hacker’s Hub. If you are starting out in Cybersecurity, check out the Hacker’s Handbook.
See you soon with another article.