
Useful Nmap Scripts for Ethical Hackers
Useful Nmap Scripts for Ethical Hackers 관련


Nmap is short for Network Mapper. It’s an open-source Linux command-line tool for scanning IP addresses and ports in a network and detecting installed applications.
Nmap allows network admins to identify devices running on their network, discover open ports and services, and detect vulnerabilities.
Here is the basic syntax to use nmap:
nmap <ip/url>
Let’s do a quick scan and see what we can find. We can use the URL scanme.nmap.org to try out a scan. Nmap allows us to use this server to practice scans.

As you can see, we have found some open ports and services. These act as entry points for further analysis or exploitation.
Nmap is usually the first tool that ethical hackers learn. Here is a full tutorial if you want to learn more about Nmap.
Nmap Scripting Engine
A key feature is the Nmap Scripting Engine (NSE). It lets users run scripts to do detailed network scans and gather specific information.
Scripts help you perform a list of actions automatically instead of performing them step by step.
These scripts cover a range of functionalities, from service detection to vulnerability scanning. In this article, we’ll look at a few useful Nmap scripts.
I’ll walk you through each script, explain what it does, and show you how to use it. By the end, you’ll have a solid understanding of how to use these scripts as an ethical hacker.
Note
This tutorial is to help you understand network security. Hacking or even scanning another server without permission is illegal.
HTTP-Enum
Imagine you’re tasked with checking a website’s security and want to see if there are any hidden pages or directories. You suspect there might be admin panels, login pages, or test files that aren’t linked on the main site.
Finding these hidden areas could reveal critical security weaknesses, such as unprotected admin pages or old files that might still hold sensitive information.
The http-enum script is used to scan a web server and find common directories and files that might be hidden from the main site navigation.
Think of it like opening doors in a building to see what’s behind each one. It searches for paths like login pages, admin panels, config files, and other directories that aren’t typically linked on the main website.
For example, a login page or an admin section may exist at specific paths but aren’t visible to regular users. This information is useful because knowing these locations can help you identify security weak points.
Here is the command to run the http-enum script:
nmap - script http-enum -p 80 <target-ip>
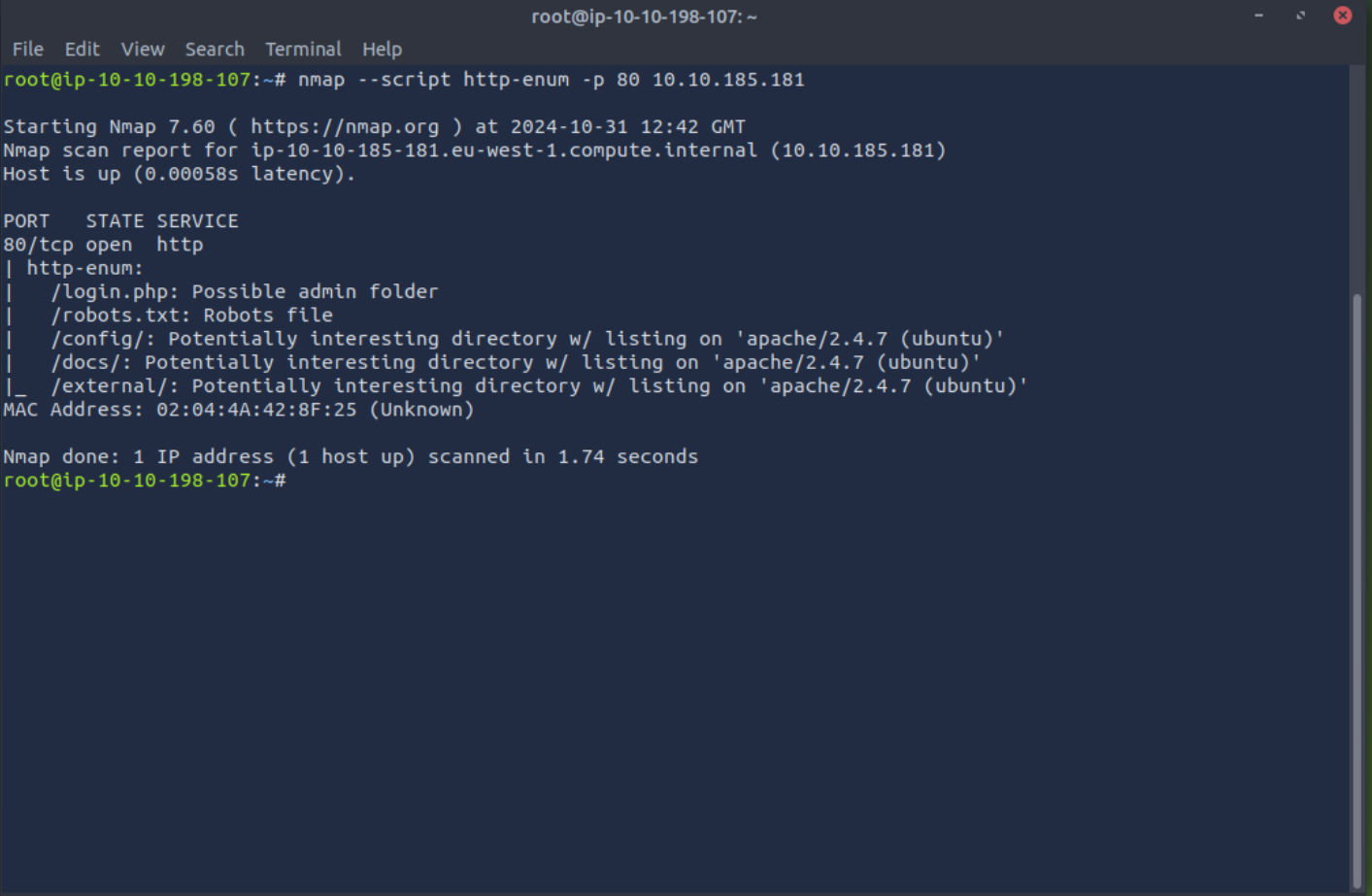
As you can see, the above sample result shows /login.php, /docs and other exposed URL paths. These can be entry points to find restricted information in a web server.
SMB-OS-Discovery
Suppose you’re exploring a company’s network to understand what kind of systems they have in place, specifically in a Windows environment.
Knowing the exact operating system and version of each server helps you assess vulnerabilities. For example, an older version of Windows might have unpatched flaws that need attention.
The smb-os-discovery script targets servers that use the SMB protocol, mainly found in Windows environments, to gather information about the server’s operating system. It can reveal details like the Windows version, the server name, and its domain.
This script helps you understand what type of system you’re dealing with, which is key for checking security flaws specific to that OS.
Here is the syntax to run the smb-os-discovery script.
nmap - script smb-os-discovery -p 445 <target-ip>
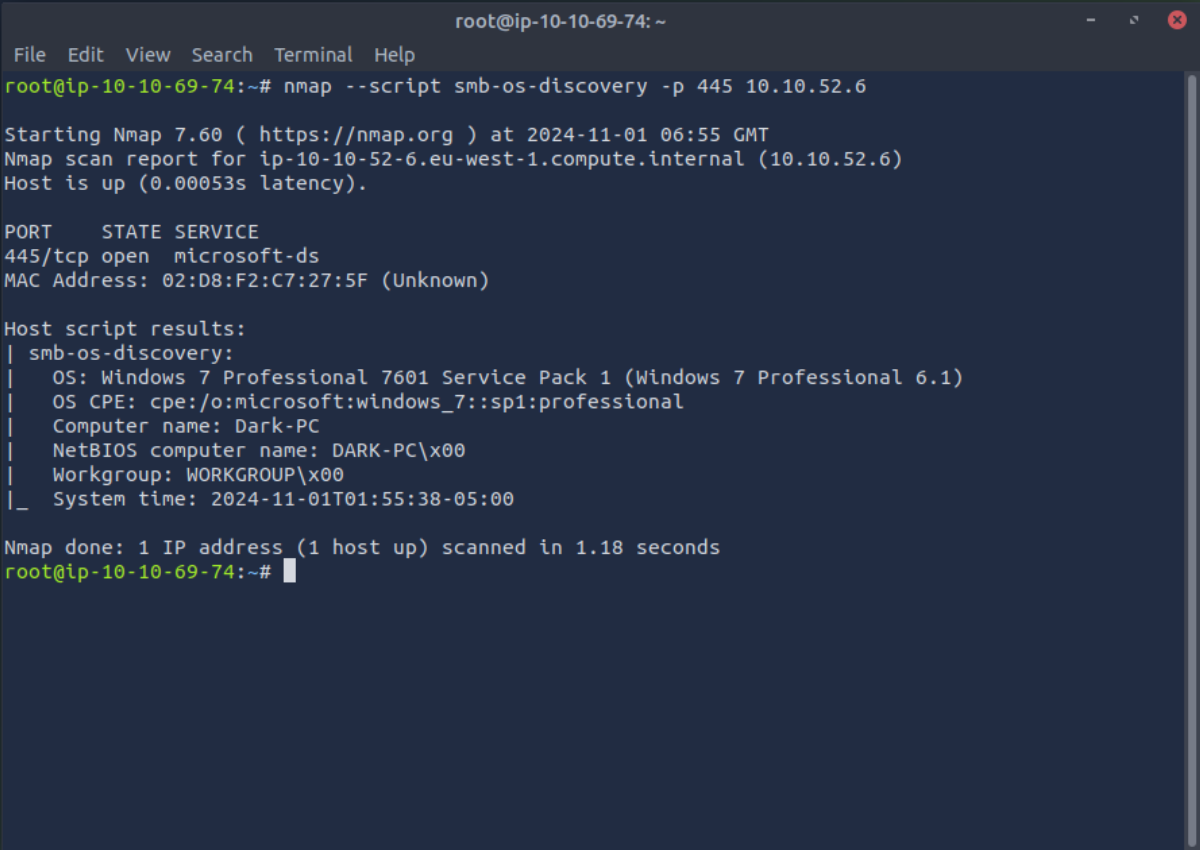
As you can see in the above sample result, the script connects to the SMB service on the target and retrieves OS information. This can help you quickly identify the Windows version and other details about the server.
HTTP-Headers
Imagine you’re evaluating a website’s configuration and security settings. You want to know what kind of server it’s running, what methods are allowed, and if it’s enforcing HTTPS connections.
These details give you insights into whether the server’s configuration aligns with best practices, helping you spot any missing security settings.
The http-headers script checks the headers sent by a web server when a user connects to it it. Headers tell you the server type (like Apache or NGINX), security settings (like HTTPS requirements), allowed methods, and caching rules.
These details are like the server’s blueprint for communication, often revealing if the server has certain protections enabled.
Here is the syntax to run the http-headers script:
nmap - script http-headers -p 80 <target-ip>
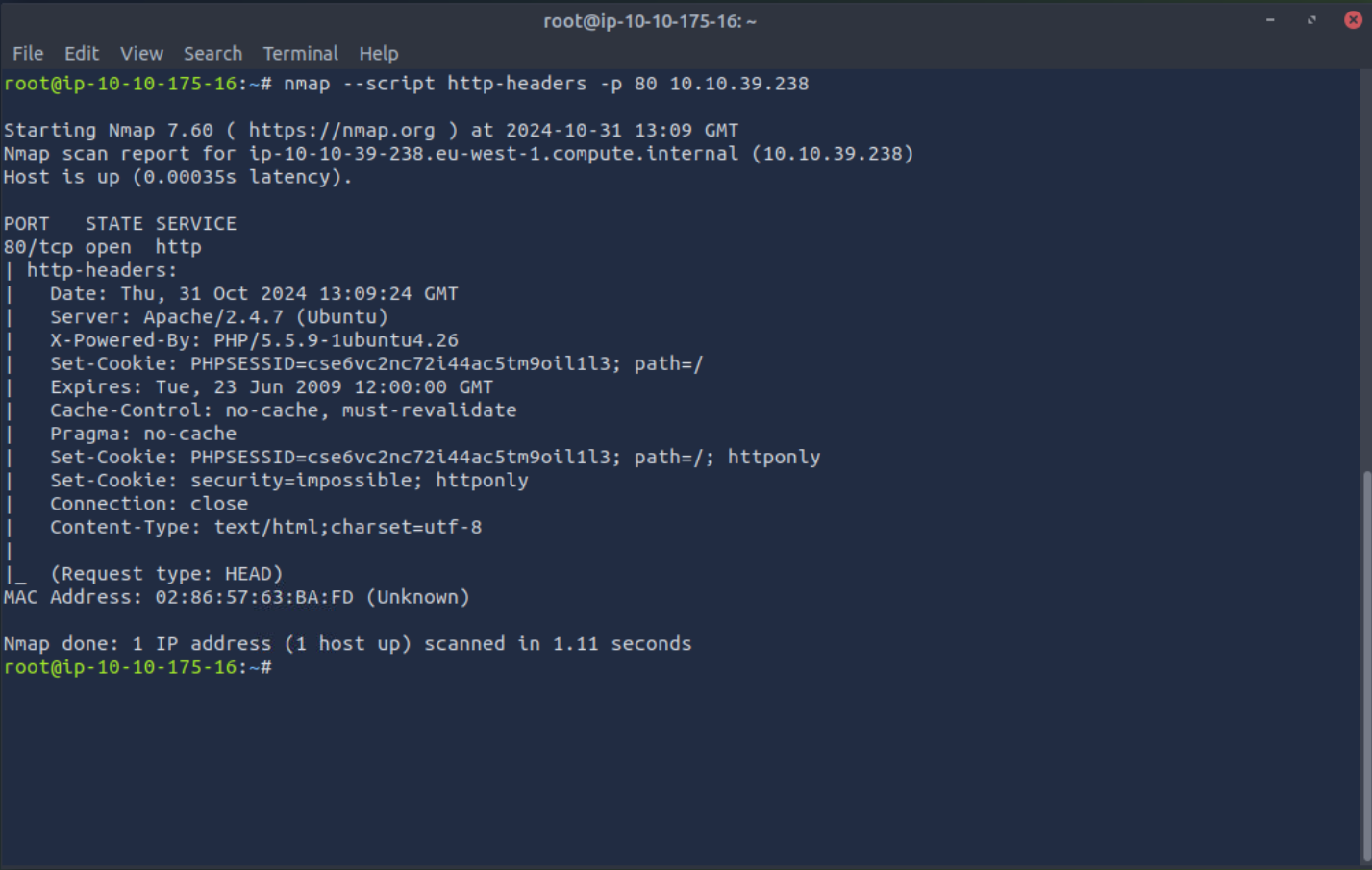
You can see that the sample response shows headers like like X-Powered-By, Set-Cookie, and so on. These headers can help to find security issues such as cross-site scripting (XSS) and clickjacking.
SSH-Brute
Let’s say you’re testing a server’s defenses against unauthorized access through SSH. You know that weak passwords are a common risk, so you need a way to check if any accounts have easily guessable credentials.
This test will help you identify weak SSH logins that need stronger passwords to protect the server.
The ssh-brute script tries to log into an SSH server by guessing usernames and passwords. SSH, or Secure Shell, is often used for remote logins.
If the usernames and passwords are easy to guess, this script might find a way in. It’s a useful test to see if login credentials are strong enough to prevent unauthorized access.
Here is the syntax to run the ssh-brute script:
nmap - script ssh-brute -p 22 <target-ip>
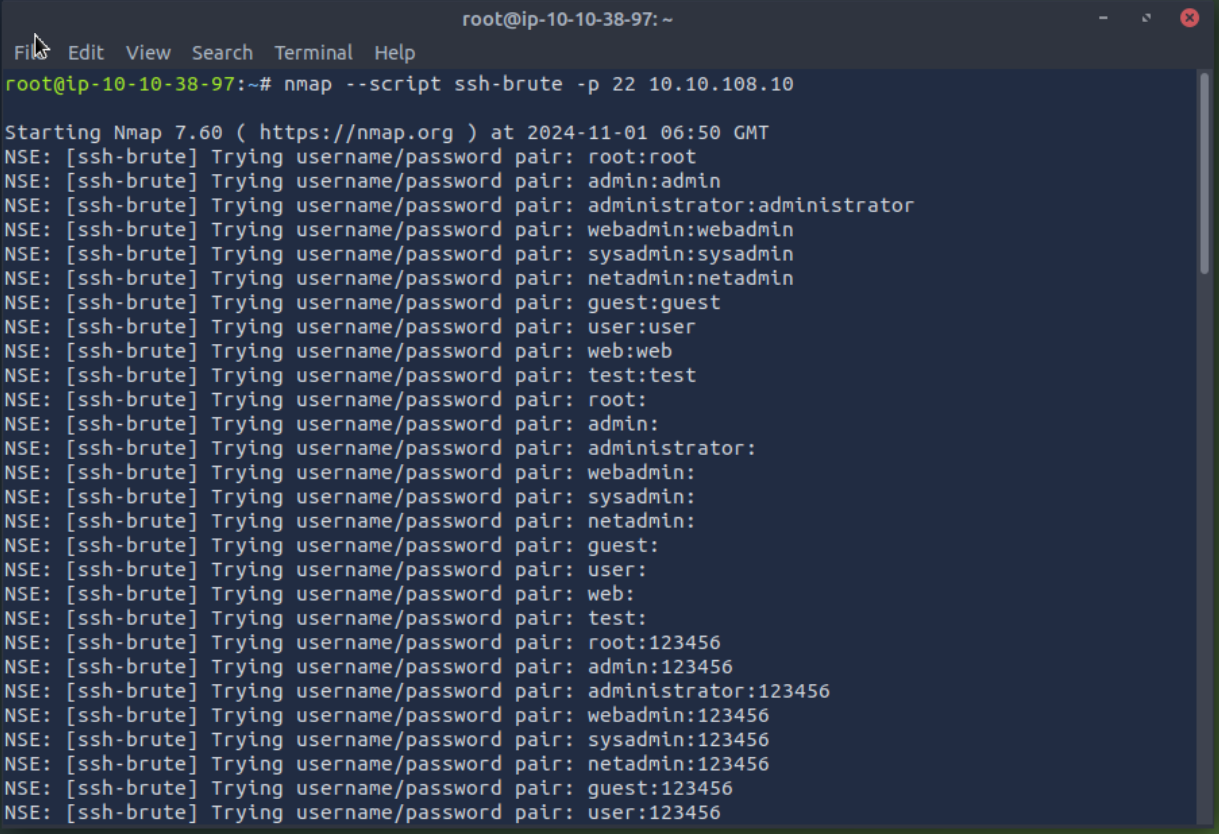
As you can see, this script tries different username-password combinations on the SSH server. If successful, it will display the correct credentials.
DNS-Brute
Imagine you’re mapping out a company’s network and want to see if they have any subdomains that aren’t publicly listed. Each subdomain might serve a different purpose, such as hosting email servers or internal testing sites.
Discovering these subdomains helps you check if any of them are exposing sensitive services.
The dns-brute script helps you find subdomains associated with a given domain by trying out common names, like “www,” “mail,” or “ftp.” Subdomains can host separate services and applications, each with its own set of vulnerabilities.
Here is the syntax to run the dns-brute script:
nmap - script dns-brute <target-domain>
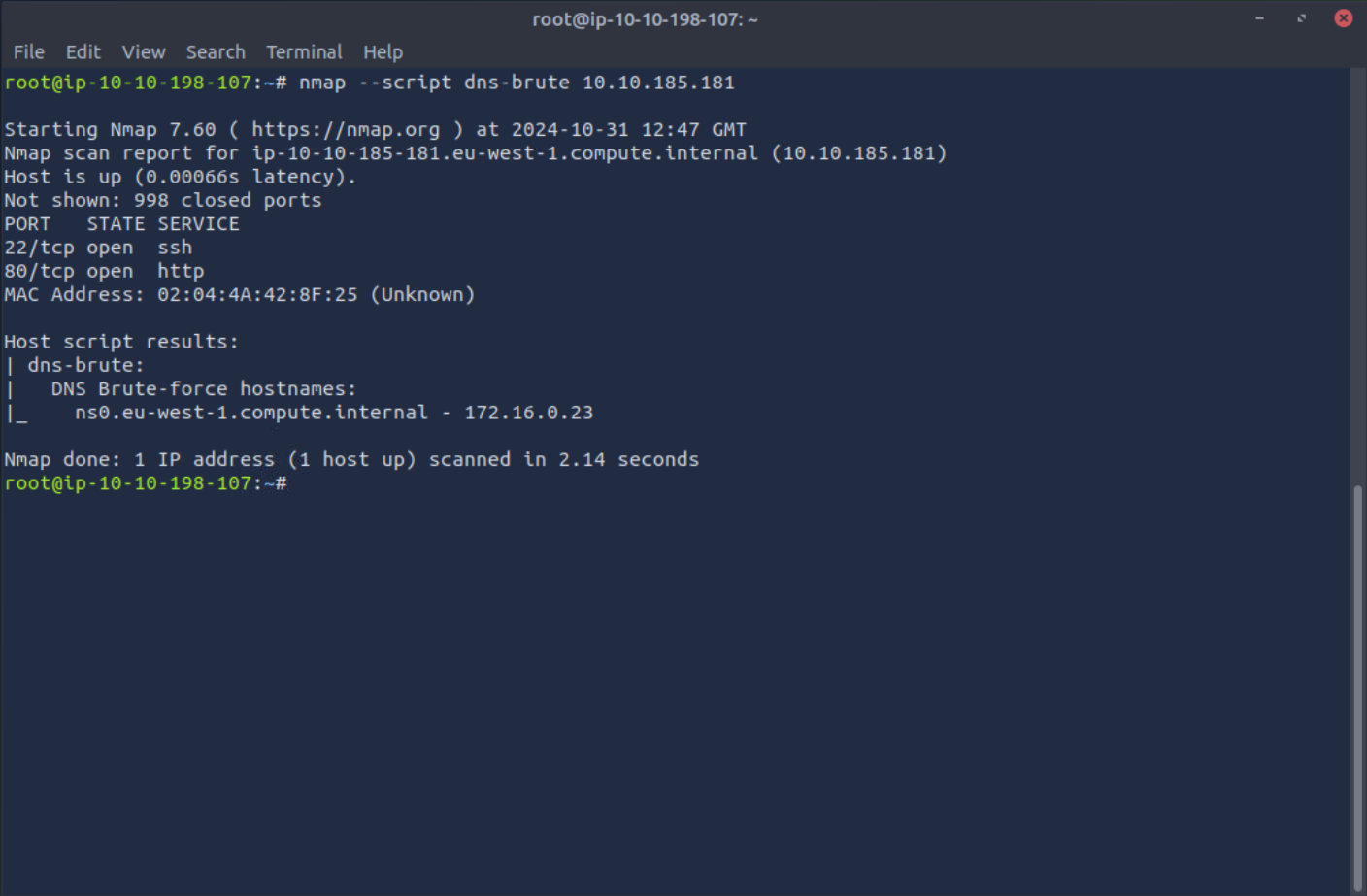
As you can see, the script attempts to resolve a list of common subdomains, and finds one internal hostname. Using this script can reveal subdomains that aren’t listed in public records, helping you to gain a fuller picture of an organization’s network layout.
Conclusion
These Nmap scripts provide a powerful way to audit, troubleshoot, and secure networks. By understanding what each script does and how to use it, you’ll be able to uncover hidden issues and safeguard your infrastructure.
Info
To learn how to build a career in Cybersecurity, check out** The Hacker’s Handbook. To practice hacking real systems and get help from other hackers, join The Hacker’s Hub.