
More Secure Authentication: From Passwords to Passkeys
More Secure Authentication: From Passwords to Passkeys 관련

In the ever-evolving world of cybersecurity, authentication remains a cornerstone. Traditional methods, like passwords and social logins, are increasingly vulnerable to attacks. Enter passkeys—a revolutionary approach promising enhanced security and user convenience.
This guide will explore the current state of authentication, delve into what passkeys are, how they work, and discuss the challenges and future of this technology.
The Current State of Authentication
Authentication is a critical component of digital security, serving as the gateway to systems and data. Despite numerous advancements, traditional authentication methods, such as passwords and social logins, remain prevalent. But these methods are increasingly proving to be inadequate in addressing modern security challenges.
Passwords, once considered the gold standard, are now recognized as a significant weak link in cybersecurity. The rise in sophisticated cyberattacks, coupled with poor password practices, has highlighted the urgent need for more robust authentication mechanisms.
Passwords are susceptible to various attacks, including phishing, brute force, and credential stuffing. Many users also recycle passwords across multiple sites, exacerbating the risk. Managing multiple passwords can be cumbersome, leading to weak password practices and forgotten credentials.
Social logins, while convenient, bring their own set of issues, including privacy concerns and dependency on third-party platforms. Users are often wary of sharing their social media credentials with third-party sites, fearing data misuse.
Also, social logins tie users to specific platforms, which can be problematic if a user decides to leave a social network or if the platform experiences an outage.
Magic links, an alternative authentication method, also have their limitations. Magic links are sent via email, which is not always secure. If an email account is compromised, so is the authentication.
The process of checking email and clicking a link can be cumbersome, particularly for users on mobile devices or with poor internet connectivity. Emails can also be delayed, end up in spam folders, or fail to deliver, causing frustration and potential access issues for users.
As the digital landscape continues to evolve, the need for more secure, user-friendly, and scalable authentication solutions becomes paramount. This exploration of the inherent problems with passwords, social logins, and magic links sets the stage for understanding why passkeys are a vital innovation in the field of authentication.
What are Passkeys?
Passkeys represent a modern authentication solution designed to address the shortcomings of traditional methods. Essentially, passkeys eliminate the need for passwords by utilizing a pair of cryptographic keys to authenticate users securely.
At the core of passkeys is public-private key cryptography. Each user has a unique pair of keys: a public key, which is stored on the server, and a private key, which remains securely on the user's device.
When a user attempts to authenticate, they use a method like biometric verification (fingerprint or facial recognition) or a device-specific security feature to access their private key.
This private key generates a cryptographic signature that the server verifies using the corresponding public key, ensuring a secure and seamless authentication process.
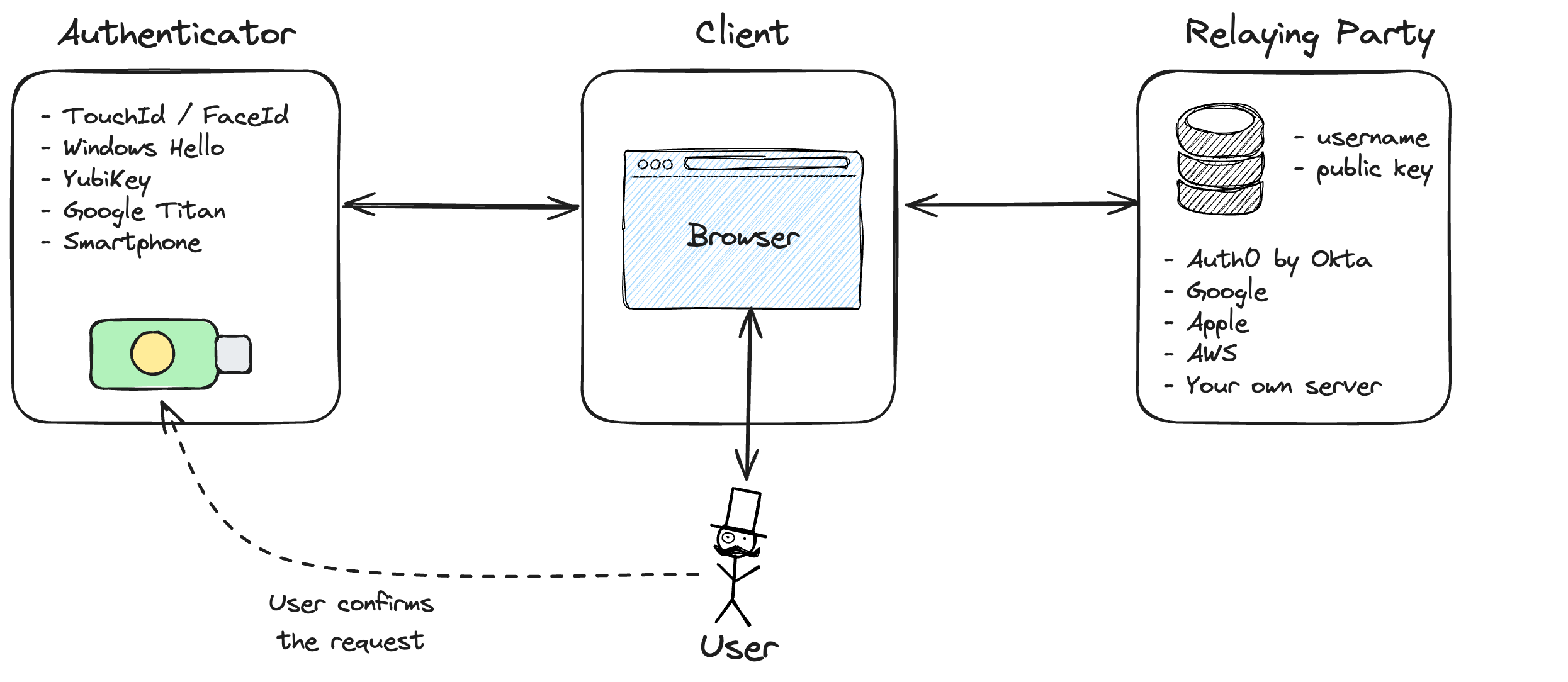
PasskeysFIDO2 standard, which promotes interoperability and security across different devices and platforms. Major tech companies, including Google, Microsoft, Okta, and Apple, support this standard, making it a robust and widely adopted solution.
The use of biometrics and device-based authentication enhances security by ensuring that the private key never leaves the user's device and is never exposed to potential attackers.
This approach significantly reduces the risk of phishing attacks, as there are no passwords to be stolen or guessed. Passkeys also help streamline the user experience by eliminating the need to remember and manage multiple passwords.
Implementing passkeys involves a few key steps:
- Registration: During account creation or passkey setup, the user's device generates a new key pair. The public key is sent to the server and stored with the user's account information.
- Authentication: When the user logs in, they use their private key to generate a cryptographic signature. The server verifies this signature using the stored public key, ensuring that the user is who they claim to be.
Info
Visit learnpasskeys.io to learn in detail how each of these processes work.
By leveraging these principles, passkeys offer a secure, user-friendly, and scalable solution for modern authentication needs. As developers, understanding how passkeys work and how to implement them is crucial in staying ahead in the realm of digital security.
Challenges with Passkeys
While passkeys offer numerous advantages over traditional authentication methods, they are not without their challenges. Understanding these challenges is crucial for developers and organizations considering adopting this technology.
Adoption and Integration
One of the primary challenges with passkeys is the integration with existing systems.
Many organizations rely on legacy systems that are not compatible with passkey technology, requiring significant overhauls to implement. Migrating to a passkey-based system involves not only technical adjustments but also changes in infrastructure, which can be resource-intensive and time-consuming.
User Education and Trust
Introducing a new authentication method requires educating users about how it works and why it's beneficial.
Users need to understand and trust the new system, which can be a hurdle given the novelty of passkeys. Ensuring that users feel comfortable and secure with the transition from passwords to passkeys is essential for widespread adoption.
Technical Considerations
Passkeys rely heavily on device capabilities. Not all devices support biometric authentication or the FIDO2 standard, potentially limiting the adoption of passkeys.
Developers need to ensure that fallback mechanisms are in place for users with unsupported devices, which can complicate the implementation process.
Compatibility and Interoperability
While the FIDO2 standard promotes interoperability, ensuring compatibility across different devices, operating systems, and browsers can still be challenging. Developers need to thoroughly test their implementations to ensure a seamless user experience across all platforms.
Despite these challenges, the benefits of passkeys in terms of security and user experience make them a compelling option for modern authentication. By addressing these challenges proactively, developers and organizations can pave the way for a more secure and user-friendly authentication future.
The Future of Authentication
The evolution of authentication is a testament to our ongoing quest for balance between security and convenience. From the simplicity of passwords to the robust security of passkeys, each step forward has been driven by the need to protect our digital lives against increasingly sophisticated threats.
Passkeys represent a significant leap in this journey, offering a secure, user-friendly alternative to traditional methods. By leveraging cryptographic keys and biometric verification, passkeys address many of the vulnerabilities that plague passwords and social logins.
The path to widespread adoption is not without its challenges, though, from integration hurdles to user education. But despite these obstacles, the benefits of passkeys make them a compelling option for modern authentication.
As developers and organizations navigate these challenges, the future of authentication looks promising. By embracing innovations like passkeys, we can move towards a more secure, seamless digital experience for all users.
The story of authentication is ongoing, and as we continue to innovate, the lessons from our past and the potential of our future guide us towards a safer digital world. Stay ahead of the curve, keep learning, and together, we can build a more secure digital landscape.
Thanks for reading!